*update - CMMC v2.0 was introduced on 11/4/2021...additional updates to this article will be included soon.
Contact Arrakis for CMMC support at [email protected], however, in the meantime, keep reading and learn a little bit about CMMC below. Arrakis is a CMMC-AB Registered Practitioner Organization (RPO) as well as a certified trainer for CMMC through PECB.
What is CMMC – If you haven’t heard of CMMC (Cybersecurity Maturity Model Certification) yet, you soon will if you are involved in any capacity on a US Government Department of Defense (DoD) project. CMMC is a five-tiered cybersecurity model where each tier involves increased maturity and additional requirements. Additionally, each tier builds on the previous tier in that in order to be recognized as mature at level 2 (ML2) you must also do everything involved at ML1. Currently only ML1 through 3 have been defined as it relates to requirements with 4 and 5 being required for the most secure and sensitive of environments…regardless ML4 and 5 are still the unknown.

Why we have CMMC is probably obvious to everyone, or at least will be, after reading this paragraph. There are entities out there that are hostile to the US Government and the American way of life. These entities could be local to the USA, domestic activists, foreign activists, foreign governments, terrorist organizations, disgruntled citizens, or any other definition of whomever/whatever is hostile to the US Government. Additionally, it is clear that some countries (i.e., China) have clear desires to compromise as many companies as possible in order to acquire technology without spending R&D money…essentially stealing technology at the expense of the USA and USA based companies. In order to cover all our bases for this collection of hostile entities, we’ll call these entities the threat in a very broad sense. It is the viewpoint of the DoD that the threat may not only attempt to compromise a large prime contractor directly but is more likely to leapfrog through subcontract companies to glean just a smidge of data that can be later compiled together to produce more sensitive information. This technique is called “island hopping”.
Because of the previous paragraph and the clear examples that have been published in the news for the last two decades, the DoD has determined that something like the CMMC is needed to help protect the security of the USA as well as help degrade the technology advancements of the threat. Just Google “industrial espionage” and “China” and you’ll see plenty of examples.
CMMC is fairly straight forward in that it is a pass/fail environment; meaning that if you did 99% of it perfectly, then you have failed. Simple. You are either 100% compliant with the CMMC published minimum standards at your desired maturity level or you are you’re not. Certainly, you can do more than CMMC requires, but some companies will likely find just meeting the standard is challenge in and of itself.
Now, is there flexibility? Yes, there is but not much and certainly far less than other regulatory environments. Should an audit team visit you as a part of a company’s certification process and they discover a “finding”, you do have some ability to remediate that finding and still pass. For example, if you couldn’t prove visitors had signed in when the audit team was there (maybe the person with the sign in book was sick that day and it was in a locked file cabinet) then you would have a finding that the audit team could then review later, over Zoom, and the finding could then be resolved, and the company would still be eligible for certification. Please also keep in mind the audit team would likely very much inquire why there was no back up plan in that particular case or inquire if visitors were simply not allowed to visit that day. Always remember that every excuse you provide to an audit team, regardless if CMMC or not, is likely to raise additional questions.
Where there isn’t flexibility is when a company simply isn’t doing something, at all, and it’s discovered by the audit team. Let’s say there is a database that wasn’t encrypted but should be. Then, when pointed out by the audit team, the company turns on encryption. In that case, suddenly generating evidence won’t be sufficient at all because the company should have been doing it for a significant amount of time prior to the arrival of the audit team. The audit team would likely then also inquire about all the other related audit subjects that could come into play (encryption policy, possibly data classification policy, encryption procedure, etc…) and fail the company there as well.
An additional area of flexibility is simply achieving the next lowest level of compliance you need. For example, Maturity Level 1 (ML1) doesn’t really require, but strongly encourages, any sort of administrative controls such as policies, standards, and procedures. Most companies do have issues with administrative controls due to lack of experienced and certified security personnel to help oversee that. In the case of ML1, a company can simply “demonstrate” security to achieve ML1 and not worry about the administrative controls. However, in this case, the company wouldn’t be allowed to have CUI data as that would require ML3.
There are also new information classification acronyms that you need to understand. Don’t worry, it’s really only two…FCI and CUI.
FCI stands for Federal Contract Information. Essentially, this is simply the “awareness” of federal contract details. Now, before I go on, some contracts are classified in such a manner that even knowing the contract exists, but not any other details, would require a security clearance above the CMMC model. Think NSA for example. Regardless, contracts that aren’t actually classified can still bear risk to the US Government by simply understanding the unclassified contract details. As an example, take any random military installation that places a one-time contract for banquet tables, PA system, and food services for 500 people in six months’ time from now. Doing a simple Google search reveals that this random military installation is predominately focused on military intelligence. The odds would likely be very high that the persons attending would likely be involved in the intelligence community thus a hostile entity may want to have surveillance of who entered the base or find a way to get a person on the food service team that serves food at the event itself, or any other reason involving surveillance. Another option would be to compromise the food service company completely and simply poison the food to take out the 500 participants. That was just an example revolving around a banquet but also consider awareness around an ammunition order or maybe the awareness of a large order of hellfire missiles and then consider why the order might have been made. A large purchase of hellfire missiles may give an indication of the start of a ground conflict somewhere using Apache helicopters. These are just some of the concerns related to FCI. The ability to handle FCI data requires at least a CMMC ML1.
CUI stands for Controlled Unclassified Information. Another way to put it, very simply, is anything that still needs to be protected from outside sources but doesn’t hold a federal classification level of at least SECRET. Essentially, this is the information that is related to the contract but is much more technical in nature. Imagine some widget that needs to be built by some private company for a communications satellite, the specs for the widget would be CUI data and because the company was building the widget, off of a contract, they would also have FCI data because of the contract to make the widget.
Now, someone is probably thinking, why don’t they just make all CUI data pushed up to the SECRET level? Great question!! The answer is that the company would then be required to have what is known as a SCIF, which is essentially a very secure area that would be equivalent to what the DoD would have to protect SECRET material on an actual military installation….and would be very cost prohibitive to companies in general. So much so that some companies simply wouldn’t be able to be involved in DoD business in any way. Larger companies likely could, but then lawsuits around monopolies would likely pop up and smaller businesses such as minority owned, woman owned, or veteran owned probably wouldn't be able to participate. Protected smaller business not being able to participate would also impact the federal funds that are specifically set aside for small businesses. It’s important to understand that, in order to interact with CUI data, you must have at least ML3.
In the interest of reducing confusion and hassle for companies, lets also discuss audit responses that absolutely wouldn’t be acceptable when the audit team is there.
Accepting risk – Not an option at all. Just because a company is choosing to not do something it should, and chooses to accept the risk instead, simply won’t fly for CMMC. Either the company is doing what it should to achieve the CMMC minimum standards (and will pass), or it isn’t (and will fail). What this will eventually boil down to, in the opinion of the DoD, is that the life of a soldier will be at risk and it would be intolerable to allow a 3rd party to just accept risk if a soldier's life is at stake.
Company culture - CMMC has specific, if not a little vague, wording that does indicates a culture that is compliant with CMMC. Honestly, CMMC could probably reinforce this a little better. The CMMC has specific language that revolves around the company being able to demonstrate habitual and persistent activities. This means that the company must be able to demonstrate to the audit team that administrative controls and security activities are deeply ingrained in company personnel.
Funding – In this case the CMMC doesn’t mince words at all. A lack of funding to become CMMC compliant clearly shows a lack of leadership support as funding comes from leadership. Again, CMMC requires compliancy in order to be compliant so if there is a requirement, even at the lowest level of ML1, that isn’t properly funded then even ML1 won’t happen. Along those same lines, if there is a thousand-person company and only one infosec guy then the auditor is likely going to wonder if leadership has properly funded the staffing of the infosec team. Additionally, if we had a 200-person organization (where having one infosec guy may be more appropriate) but has global locations, the audit team may wonder how a single person can perform 24/7 operations without sleeping. Essentially, the audit team is experienced enough to know what personnel and technology should be properly funded for a company of a particular size. There must be leadership buy in at all levels to make this happen.
Experience and certifications – In some companies it’s not uncommon to see someone who was spontaneously designated the Information Security Officer, the Data Privacy Officer, etc.… without any actual experience or certifications in the new specialties suddenly thrust upon them. I call this person a sacrificial lamb and I have no doubt that some of the readers are either chuckling because they have experienced it or suddenly cringed because they are still experiencing it. This is a no-go in the CMMC world. Control AT.2.057 specifically states “ensure that personnel are trained to carry out their assigned information security related duties and responsibilities.” This means a few things:
- You have to be able to prove that training occurred, one way to do that is to show you sent someone to training or the person hired is already certified which implies training occurred (otherwise there would be no certification).
- Regardless of the previous item, this also means that the person must be able to demonstrate their job in a manner that it appears to be natural to the auditors. Thus, throwing someone in the fire at the last minute would mean that the auditors would likely be less than impressed. This also removes all those really good test takers with no hands-on experience (I'm sure some readers also know some of these guys as well).
- These activities also apply to technology that your company may have. So, assuming you had one information security person, then this same person must show competency with these technologies used by the information security program. In other words, you can’t apply some new technology that the infosec guy barely knows and expect happy auditors.
- Finally, there is nothing that indicates you have to have employees perform all of these functions; you can outsource but will need to do your due diligence on the outsourced entities based on exactly what role they will be performing. For example, Arrakis Consulting could be the entity that helps implement and manage your administrative controls through our platform. In that case, Arrakis Consulting wouldn’t have access to any CUI data and wouldn’t need to demonstrate to the company an ML3 maturity. This would leave that entire section out of the responsibility of that lone ranger infosec guy. You can even go so far as to bid on CUI related contracts but then subcontract the CUI work out to an ML3 subcontractor where the prime doesn’t even see the CUI.
There are a few gotchas as well. In other words, there are a few areas that will certainly bite you if you aren’t fully aware of them. Finding out the hard way can be very expensive for your company. See below:
- Administrative controls, such as policies or procedures, that conflict with what is actually being done. So, let’s say that your policies and procedures indicate encryption must be used and how it must be used along with why it should be used but isn’t actually being done…that would definitely be a gotcha as administrative controls are the foundation for any security or privacy program. The audit team would naturally conclude that you don’t actually do what you say you do which would also lead them to believe that security activities were not habitual or persistent or, possibly, being performed without the awareness of leadership. To make it worse, once you open that can of worms, the audit team will naturally start to question everything else you are doing. The only caveat to this is ML1, where administrative controls aren’t even required, however if there are administrative controls in ML1 they must not contradict demonstrated ML1 activities.
- Not enough evidence can always get you. Saying you do something isn’t the same as being able to prove you’ve done something multiple times over the last few months without some sort of auditable system of record. The audit team is obligated, by CMMC, to pull evidence by two of three methods; interview, documentation, and testing. About the only possible loophole in this area, however, would be extremely risky, and would require the auditor to agree to shoulder surf during control testing to see clearly that the person performing the activity showed no confusion on how to perform the task in addition to interviewing enough people to believe that the activity has happened that way consistently. We advise against taking such a gamble.
- Assuming you will become certified in a very short timeframe is likely going to be a gotcha. Let’s assume that you want to handle CUI data, that would require at least ML3 however that means you would have to demonstrate “habitual and persistent” activities for all areas of ML3 and below. There are 130 controls and involve all types of internal personnel, is it really possible to get that level of maturity quickly? Likely not.
- Not fully implementing a specific required area but having a plan to implement that required area is also a failure. At the time of the audit, you must be performing all required controls, or you won’t pass that area which leads to overall failure. Planning to do something doesn’t count as actually doing it. Also, having a dependency on a tool that the company doesn’t own is equally a failure.
- Not performing proper due diligence on your employees or your subordinate vendors. You will be expected to be able to prove this was done and is in alignment with your onboarding policy and procedure. Unfortunately, in today’s world, companies are not fully performing due diligence upon hire or internal assignment. To compound that issue, in some states (California) it is illegal to refrain from hiring someone based on their criminal history…yet if you don’t consider that you could be in violation of CMMC. A possible loophole would be to simply not operate in California.
- Being under the assumption that you can apply a tool or some form of technology to solve a problem that a human can’t. While that sounds great, that tool or technology must be managed by a human and the company must ensure the personnel assigned to perform the task can understand the tools and techniques in a manner where it is clear they are trained and can survive an auditor's interview.
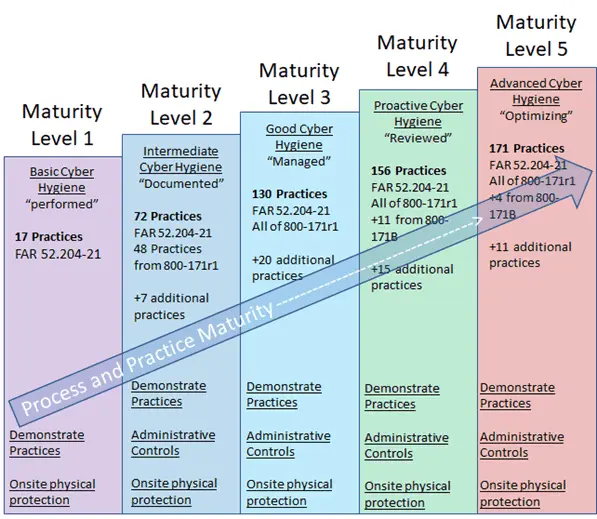
Now that we have gone through the above, let’s talk about maturity. CMMC is broken into 5 different maturity levels with requirements coming from multiple sources. Sources such as FAR 52.204-21, NIST 800-171 (including subsets), as well as various additional requirements added in to supplement what the DoD felt was missing. Each maturity level has increasing requirements where the next highest level requires you to fulfill the desired level and all lower levels.
Maturity level 1, as previously discussed, is the lowest and easiest to comply with as the company only has to demonstrate activity that meets the requirements but doesn’t have to provide administrative controls such as policies or procedures…which are still strongly recommended though. There are 17 practices found in ML1 with all being pulled from FAR 52.204-21 . FYI, a practice is something that is being done but not necessarily fully documented or matured.
Maturity level 2 is where it starts getting more intense for the company seeking certification. We jumped from 17 practices to 72 and picked up most of them from NIST 800-171. At this stage, ML2 requires documented policies and procedures and the company must demonstrate habitual and persistent activity. Ad-hoc activity isn’t permitted and activity that is performed must be auditable. Thus, if you don’t have an auditable system of record for activities that are being performed, then you should get one.
Maturity level 3 again increase difficulty almost two-fold by requiring 130 practices with all practices from NIST 800-171 being in play and an additional 20 practices that indicate good cyber hygiene on the part of the company.
Amazingly, ML4 only has 156 practices (currently) as opposed to doubling like ML3 and ML5 is currently at 171 practices. Why did we group those together and emphasize “currently”? Well, it’s because the CMMC hasn’t fully fleshed out ML4 and 5 and both could change.
One thing to point out, regardless of maturity level, all the physical security controls require an on-site visit by the audit team and all the physical security controls are contained in ML1. This is unavoidable.
The Audit Process is pretty similar to an ISO or SOC2 audit in that there are independent teams performing functions to reduce chances of a conflict of interest.
To increase chances of success, the company seeking certification is suggested to contract with an experienced 3rd party that would help them get ready for the audit (such as Arrakis Consulting). This is called pre-assessment readiness and can save a lot of time, money, and reduce stress during the actual audit. Ideally, at this point, we really don’t even want CMMC to know we are seeking certification as we really don’t know how long it will take the company to become compliant enough to pass a certification audit.
Once the company is ready, then the company reaches out to a C3PAO entity (aka an independent company that can perform audits on behalf of CMMC) and validates that they are in good standing with CMMC. If not in good standing, then another C3PAO is required.
After a contract is signed with the C3PAO, the C3PAO makes a request to the CMMC for an assessment ID that is tied to the company for that particular assessment. Then the C3PAO assigns an audit team that is comprised of people certified to perform an audit of that maturity level. For example, an auditor certified for only ML1 can’t do ML3 but an auditor for ML3 can do ML1-3. This audit team performs the audit, generates a report, and sends to the C3PAO for QA review. Assuming no discrepancies, the C3PAO submits the report, assessment ID, audit team IDs, and certification recommendation of either pass or fail. If the recommendation is a “fail” then no further review is performed by CMMC however the company can then file a dispute to seek an alternate outcome. Assuming a recommendation of “pass” then the CMMC performs another QA review and, if the CMMC agrees, will issue a certification to the company. After certification, the CMMC updates the corresponding database that indicates the company has met a specific maturity level.
There are also various areas to prevent conflict of interest. For example, the team that got the company ready can’t participate in the audit itself. The audit team can’t provide advice or guidance during the audit. If the C3PAO is also a company that helps client companies get ready for an audit, then the entire company can’t be involved in the actual audit. So, from a business standpoint the C3PAO really needs to determine if they want to be in the helping business or the audit business on a case-by-case basis.
What should also be understood is who exactly gets interviewed as a part of the audit. The actual person performing the activity will get audited. No more will a manager represent someone in an audit to indicate what the employee is doing…now, the employee themselves will get interviewed by the audit team in a private setting. While it could be considered that the employee is concerned about reprisals for telling the truth, it should also be understood that the audit team wants to hear the relevant information straight from the person who performs the activity.
What can go wrong should also be considered. We already discussed conflict of interest and the possibility there but there are also other areas that could be an issue. First, the company should never allow evidence that contains CUI to leave their premises nor should an audit team request CUI evidence. Doing so, for both, defeats the purpose of CMMC and should be reported as soon as possible.
However, there are some other areas that the company should seriously consider as it relates to possible sanctions. Any auditor can tell you that at some point in their career a company has asked the auditor to look the other way. That simply can’t happen and opens up the company and auditor to legal sanctions. Any auditor can also tell you that there is always going to be some company that is “less than truthful” on some evidence or possibly telling either a prime contractor, or the DoD itself, that the companies security posture was something other than what it really was. This is called a violation of the False Claims Act, which essentially is any entity/person that makes a false claim in relation to a government contract and can have some hefty financial penalties in addition to possible criminal charges. To hit the point home, the Department of Justice received more than $3B in settlements for 2019 alone because of this. So how did the DoJ find out? Well, whistleblowers get between 15-30% for reporting false claims. When you think of how many millions some contracts are worth, even 15% is an instant retirement. Cisco was fined $8.6M and 15% of that is $1.3M as a whistleblower award.
Not to forget, but there is also the “Christian Doctrine” which essentially is a doctrine that states that any entity that signs a government related contract should know they must protect information (such as FCI or CUI) regardless of if it was actually written in the contract or not. Essentially, just because you don’t know, or it’s not spelled out in the contract doesn’t mean you can avoid what you should be doing…even if you didn’t know you should be doing it. FYI, this is pretty much across all government contracts.
There is also the prime/subcontractor relationship that has to be considered because every upstream company is obligated to ensure that any downstream company is compliant with the appropriate CMMC maturity level in order to collaborate on DoD contracts. The liability for a company not performing the appropriate due diligence on downstream companies can be great and fall under the False Claims Act and the Christian Doctrine simultaneously.
Prediction – Arrakis Consulting predicts that all federal contracts will soon have some form of CMMC language or requirement once CMMC is fully enforced. This prediction is simply because there are too many interconnections between companies that eventually lead to government contracts. Additionally, NARA is the government body that provides the definition of what CUI means...and it is vast...so much that it is clearly far beyond just the scope of the DoD. Arrakis Consulting also predicts, that highly sensitive state and local government contracts will have a high likelihood of the same effect. Specifically, contracts involving state entities such as revenue or taxes, prisons, health, etc…
Now for a pick me up bit of good news. 2026 is when the CMMC will be fully implemented across all DoD contracts. Start getting ready if you haven’t already.
Arrakis can help you become more compliant or remain compliant by offering an unbiased 3rd party assessment that is specifically tailored around the framework or regulation you are required to conform to as well as help reduce your overall risk.
Additionally, Arrakis can provide regulatory or compliance training to your company to help better prepare you for a regulatory environment. Click here to see just some of our options to train you in regulatory compliance.
These solutions can be in several forms:
3rd party audits and assessments - All major frameworks require a 3rd party assessment to be performed in the areas of vulnerability assessment, risk assessment, or 3rd party audit of your information systems. Arrakis can be your trusted advisor that will provide an unbiased and brutal honesty assessment of where you feel weak or where you feel a regulatory agency may target you. Don't be caught short in high risk compliance areas like GDPR, FFIEC, FISMA, etc...
Business Impact Analysis (BIA) - As a matter of good practice, a BIA should be done at least yearly to ensure that you completely understand the level of impact to your business should any portion of your business process fail. How long can you stay down without major incident? How long can you stay down before your customers decide to move to another solutions provider? Knowing the impact, both qualitative and quantitative, to your business is vital and required. Arrakis can help you realize exactly what your impact is.
Gap Analysis - regardless of what framework you are required to follow there is always something that needs to be reviewed to see where your gaps, or weaknesses, are so you have targeted and actionable items to focus your remediation or improvement efforts. Don't be caught short in high risk compliance areas like GDPR, FFIEC, FISMA, NIST, etc...
Framework implementation, consultation, or support - All companies that process regulated data are required to conform to some security framework. Whether it be NIST 800-53, NIST 800.171, ISO 27001, FFIEC, etc... we can help implement or provide consultation services to make your current implementation easier. Additionally, in several situations, companies have to conform to multiple frameworks or create a hybrid framework that reduces the regulatory risk to the company and executives. Arrakis can help guide you down the path of confusion to a clear outcome.
vCISO/CISO as a service - Some companies simply do not have the budget, experience, or training to have a CISO or an information security department. While all frameworks require a security department and a CISO it simply isn't in the budget or there isn't enough technical work to justify hiring the appropriate personnel. Arrakis can help you be acting as a trusted advisor to the CIO or COO to your company and essentially performs CISO functions. Technically, by the frameworks, someone in the company still must have the title of CISO however none of the frameworks indicate that the actual "work" can't be outsourced to a reputable 3rd party. Don't be caught short in high risk compliance areas like GDPR, FFIEC, FISMA, etc...
vCIO/CIO as a service - Similar to the CISO as a service bullet item, some companies are more focused on building their business and increasing their profit margin and just don't have the time or experience to perform CIO functions. They have strategy without execution because of a lack of ability to execute. Arrakis can help be the IT glue that binds all the technological functions into a cohesive package to fill this gap. The professionals at Arrakis have, on average, over 20 years of experience in all aspects of IT including managerial functions such as budgeting, project management, and process improvement.
Governance, Risk, and Compliance - Regardless of what framework your company is required to follow or the level of maturity all companies bear some risk because they are in business. Our GRC people can help your company stay in compliance with regulations, assess and track risk to your company, and provide an easy to follow governance model to ensure that your company operates in a stable manner that keeps the auditors happy. Don't be caught short in high risk compliance areas like GDPR, FFIEC, FISMA, etc...
Policy Creation and Review - Quite often companies have some form of policies in place but a majority of the time those policies simply do not meet the requirements of the auditors or the required frameworks the company is supposed to follow. While the intention of the company is to be compliant, the deficient policies do not help and only bring closer attention of the auditors. Arrakis has years of experience writing policy and can help bring you up to speed with the frameworks and provide for an easier success rate when it is time to be audited.